3.6 Monitoring disk space
Since the 15APR92 release of 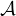
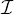
 , the availability of data areas via NFS has vastly increased the amount of disk
space accessible from a given
, the availability of data areas via NFS has vastly increased the amount of disk
space accessible from a given 
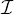
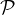
 session. The da= command line option to the aips command allows you to
specify “disks” (data areas) from many hosts in addition to the current host, subject to a maximum of 35 disks per
session. Note, however, that the BADDISK adverb has a limit of 10 disks. Thus, if more than 10 disks are accessed via
NFS, you will not be able to prevent one or more from being used for scratch files. This can be important. Reading
data over NFS is relatively efficient, but writing data is not. Even file creations (under Unix) require the writing of
zeros to the whole file in order to guarantee later access to the requested space. Over NFS, this can be a slow
process. For example, if user disk 1 is accessed via NFS, then every line of the message file must be
written with NFS, a process which has been observed to require about one second of real time per
message!
session. The da= command line option to the aips command allows you to
specify “disks” (data areas) from many hosts in addition to the current host, subject to a maximum of 35 disks per
session. Note, however, that the BADDISK adverb has a limit of 10 disks. Thus, if more than 10 disks are accessed via
NFS, you will not be able to prevent one or more from being used for scratch files. This can be important. Reading
data over NFS is relatively efficient, but writing data is not. Even file creations (under Unix) require the writing of
zeros to the whole file in order to guarantee later access to the requested space. Over NFS, this can be a slow
process. For example, if user disk 1 is accessed via NFS, then every line of the message file must be
written with NFS, a process which has been observed to require about one second of real time per
message!
Another aspect of the new disk allocation system is a scheme by which the local 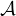
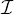
 Manager may restrict the
availability of some disk areas to a set of user numbers, specified on a disk-by-disk basis. Managers usually use this
tool to set aside most disks on a staff member’s workstation for his/her sole use and to reserve space for visitors
or other special projects on “public” workstations on a case-by-case basis. Use the FREESPAC verb
within AIPS to show you the space used and available on all disks for your session and also to show
whether or not that space is reserved. The right-most column of FREESPAC’s output will show Alluser if
the space is not reserved, Resrved if you are one of the users for which the space is reserved, Not
you if you are not allowed to use the space, and Scratch if the space is to be used only for scratch
files. Use FREESPAC often to keep track of how much space is available and where the space can be
found.
Manager may restrict the
availability of some disk areas to a set of user numbers, specified on a disk-by-disk basis. Managers usually use this
tool to set aside most disks on a staff member’s workstation for his/her sole use and to reserve space for visitors
or other special projects on “public” workstations on a case-by-case basis. Use the FREESPAC verb
within AIPS to show you the space used and available on all disks for your session and also to show
whether or not that space is reserved. The right-most column of FREESPAC’s output will show Alluser if
the space is not reserved, Resrved if you are one of the users for which the space is reserved, Not
you if you are not allowed to use the space, and Scratch if the space is to be used only for scratch
files. Use FREESPAC often to keep track of how much space is available and where the space can be
found.
Disk space is still generally at a premium. If more than one user has access to the disk areas you are using, or you
use more than one user number to separate projects, then another useful tool for monitoring disks is the
 task called DISKU. To run it, type
task called DISKU. To run it, type
> USER 32000 ; INDISK 0 C R | to get all disks and users. |
> BADDISK 0 C R | to allow all disks; can be used to skip chosen disk numbers in
31DEC23. |
This will (eventually) list on the AIPS monitor (and the message file) the amount of data space in use by each user
for all 
 disks. Identify the worst disk hogs and apply appropriate peer pressure. If you are, mysteriously, the
culprit on some disk, then
disks. Identify the worst disk hogs and apply appropriate peer pressure. If you are, mysteriously, the
culprit on some disk, then
> USER 0 ; INDISK n C R | where n is the mysteriously eaten disk |
> DOALL m ; GO DISKU C R | to run the job, listing all catalog entries requiring more than m
Megabytes. |
will give you the size of your larger files on the specified disk. Armed with this information, you may be able to
take appropriate action upon your own data.
Sometimes the available disk space has been eaten up by 
 scratch files that are no longer in use. Tasks that
abort while executing (and other mysterious events) may produce this situation. To delete all your scratch files,
except those for tasks which are still running, type:
scratch files that are no longer in use. Tasks that
abort while executing (and other mysterious events) may produce this situation. To delete all your scratch files,
except those for tasks which are still running, type:
> SPY C R | to see which tasks are running. |
> SCRD C R | to delete the files. |
SCRDEST is run automatically whenever EXIT, KLEENEX, RESTART, or ABORT task_name are executed. Note that the
imaging and deconvolution tasks IMAGR, APCLN, and VTESS, the data editor TVFLG, the sorter UVSRT and other tasks
may create large scratch and “work” files, so you should watch for “dead” copies of scratch and work files from
these programs in your disk catalog. Both MCAT and UCAT will show scratch files as well as the requested file type,
but SCAT will be easier to use. Note too that, if you are using more than one computer on a given disk area, only
those scratch files created by your current computer will be deleted when you run the SCRD verb. Work files
have to be deleted individually since they can be still of use after the task which created them has
finished.
Chapter 11 of this  ook
ook ook tells you how to backup or delete your own data to relieve disk crowding. At present,
all other methods for managing disk space involve system-dependent commands of one sort or another. Since these
may have unexpected consequences they are not recommended.
ook tells you how to backup or delete your own data to relieve disk crowding. At present,
all other methods for managing disk space involve system-dependent commands of one sort or another. Since these
may have unexpected consequences they are not recommended.
 , the availability of data areas via NFS has vastly increased the amount of disk
space accessible from a given
, the availability of data areas via NFS has vastly increased the amount of disk
space accessible from a given 
 session. The da= command line option to the aips command allows you to
specify “disks” (data areas) from many hosts in addition to the current host, subject to a maximum of 35 disks per
session. Note, however, that the BADDISK adverb has a limit of 10 disks. Thus, if more than 10 disks are accessed via
NFS, you will not be able to prevent one or more from being used for scratch files. This can be important. Reading
data over NFS is relatively efficient, but writing data is not. Even file creations (under Unix) require the writing of
zeros to the whole file in order to guarantee later access to the requested space. Over NFS, this can be a slow
process. For example, if user disk 1 is accessed via NFS, then every line of the message file must be
written with NFS, a process which has been observed to require about one second of real time per
message!
session. The da= command line option to the aips command allows you to
specify “disks” (data areas) from many hosts in addition to the current host, subject to a maximum of 35 disks per
session. Note, however, that the BADDISK adverb has a limit of 10 disks. Thus, if more than 10 disks are accessed via
NFS, you will not be able to prevent one or more from being used for scratch files. This can be important. Reading
data over NFS is relatively efficient, but writing data is not. Even file creations (under Unix) require the writing of
zeros to the whole file in order to guarantee later access to the requested space. Over NFS, this can be a slow
process. For example, if user disk 1 is accessed via NFS, then every line of the message file must be
written with NFS, a process which has been observed to require about one second of real time per
message!

